An alternate method to resolve this issue is as follows: Windows is trying to load this file s but cannot locate it since the file was mostly likely removed during an anti-virus or anti-malware scan. Tell us about your experience with our site. When the email looks legitimate, not every time it is sent from the company or service, it seems to be sent from. These programs have initiated various problems for PC users because they have the ability to hide deep inside the system and cause continuous redirects, slowdowns, and similar issues. During the full scan on the computer, all threats get deleted. Although DLL files are a dynamic link library files used to hold various codes and procedures needed for Windows programs, this is a file associated with an unwanted and possibly malicious program. 
| Uploader: | Nijin |
| Date Added: | 3 December 2008 |
| File Size: | 62.27 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 42886 |
| Price: | Free* [*Free Regsitration Required] |
Indicate the purpose of this file by scanning the system thoroughly, and remove BackgroundContainer. You can check if BackgroundContainer. If the file is associated with the unwanted application — you can freely remove it from the computer.
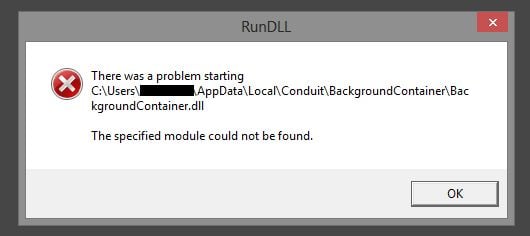
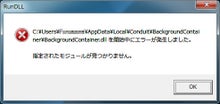
Run DLL error message/background container.dll
How to resolve BackgroundContainer. If that is the case, you should eliminate Background Container. You need to remove this registry entry so Windows stops searching for the file when it loads. If you see an entry you te to keep, return to AdwCleaner before cleaning The ad-supported program gets access to search queries, IP addresses, location, most viewed sites, and similar information. This is the easiest way to spread PUPs because freeware providers can bundle their products and make sure that all packed programs get automatically installed.
Try to avoid clicking on any redirects, pop-up advertisements or banners delivered on the screen. I actually had two popups.
When it comes to malicious files and more severe malware that can be hidden behind a common type of DLL or EXE conduit/bxckground, the distribution methods involve spam email campaigns. However, the appearance of RunDLL error message may also mean that Conduit virus or some of its leftovers are hiding somewhere inside your computer.
boot - How to resolve error on startup? - Super User
During the full scan on the computer, all threats get deleted. Sign up using Facebook.
This way you can prevent any unwanted infiltrations. Active 3 years, 9 months ago. Constant errors indicate the potentially unwanted program, in this case — a browser hijacker that is called various names: Contact Linas Kiguolis About the company Esolutions.
Subscribe to RSS
Post as a guest Name. Although DLL files are a dynamic link library files used to hold various codes and procedures needed for Windows programs, this is a file associated with an unwanted and possibly malicious program.
Email Required, but never shown. Related with browser hijacker, other PUPs Symptoms Causes system errors, unwanted content, advertisements, redirects.
Thanks for your feedback, it helps us improve the site. Improving the question-asking experience.
conduit/backgrounc You should beware red flags like file attachments, services you don't use as senders. These programs have initiated various problems for PC users because they have the ability to hide deep inside the system and cause continuous redirects, conduir/background, and similar issues.
Adware Ransomware Browser hijacker Mac viruses Trojans. This entry was posted on at Close all windows, reboot computer The result is no more error on start up. Unwanted programs like Background Container. How satisfied are you with this reply? This site in other languages x. You can choose Advanced or Custom installations and avoid cyber infections.
Even a smallest amount will be appreciated. Potentially unwanted programs like hijackers or rogue tools, adware come to the targeted system via insecure installations, when the user chooses to go for Recommended or Quick installations.
In addition to that, Background Conxuit/background.

No comments:
Post a Comment